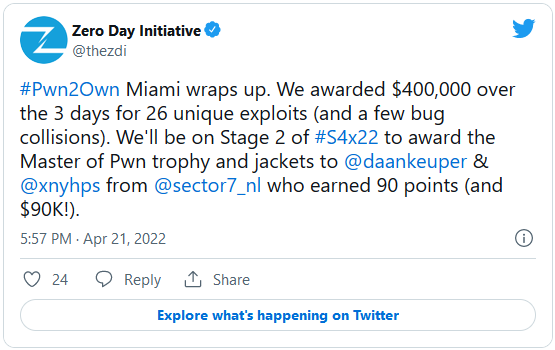
Pwn2Own Miami 2022 has come to an end, with competitors racking up $400,000 in 26 zero-day exploits (and several bug conflicts) against ICS and SCADA products in the competition from April 19th to April 21st.
Security researchers target several production categories: control servers, OPC Unified Architecture (OPC UA) servers, data gateways, and human machine interfaces (HMIs).
“Thank you again to all the entrants who entered. Without them, we wouldn’t have the competition,” Trend Micro’s Zero Day Initiative (ZDI) said today.
“Thanks also to the participating vendors for their cooperation and for providing fixes for bugs disclosed throughout the competition.”
After security flaws exploited during Pwn2Own are reported, vendors have 120 days to release patches until ZDI publicly discloses them.
Winner Prize $90,000
The winner of the Pwn2Own Miami 2022 event is Daan Keuper (@daankeuper) and Thijs Alkemade (@xnyhps) from Computest Sector 7 (@sector7_nl).
On day one, they made $20,000 after executing code on an Inductive Automation Ignition SCADA control server solution using a missing authentication vulnerability.
On the same day, they used an uncontrolled search path vulnerability to gain remote code execution (RCE) in the AVEVA Edge HMI/SCADA software and were awarded $20,000 for their efforts.
The next day, Computest Sector 7 used an infinite loop condition to trigger a DoS state against the Unified Automation C++ demo server and earned $5,000.
Last but not least, on day two of Pwn2Own Miami 2022, the team bypassed the OPC Foundation OPC UA .NET standard for trusted application checks and added $40,000 to their reward.
They earned a combined $90,000 over three days of competition and earned the title of Master Pwn by taking the top spot on the leaderboard with a total of 90 points.
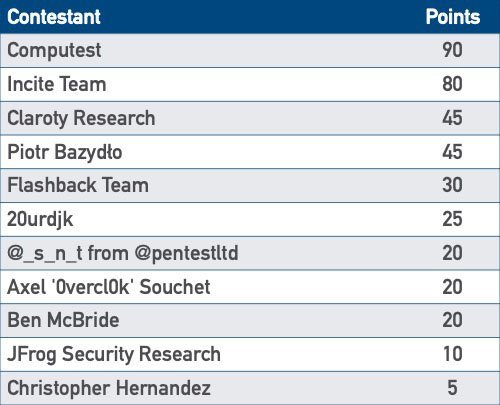 Pwn2Own Miami 2022 Results (ZDI)
Pwn2Own Miami 2022 Results (ZDI)
This year’s Pwn2Own Miami was held in person at the S4 conference in South Beach, Miami, and also allowed remote participation.
During the first edition of the ICS-themed Pwn2Own Miami in January 2020, ZDI awarded $280,000 for 24 unique zero-day vulnerabilities in ICS and SCADA products.
You can watch a recording of the Computest Sector 7 (@sector7_nl) team working on the OPC Foundation OPC UA .NET standard below.
ZDI described their attempt as exploiting “one of the more interesting bugs we’ve seen at Pwn2Own.”